Ransomware: Statistics, Latest Threats and Countermeasures

by Pouya Ghotbi, Associate Director of M.S. in Cybersecurity Program
The cyber security threat landscape has evolved over the past few years. Attackers have shifted their focus from complex high-effort breaches to more simple attacks that extract revenue in significantly less time.
A relatively new trend that is becoming more prevalent is ransomware. One of the latest ransomware threats, the Colonial Pipeline attack in May embodies how things can go wrong very quickly. System disruptions forced the company to shut down its pipeline, causing major disruptions to gas delivery up and down the East Coast of the United States. People suffered as the lack of fuel supply caused prices to soar nationwide.
The St. Bonaventure University team ran a webinar earlier this year to review widespread cybercrime events and their Indicators of Compromise (IoC). This blog summarises the key points from that discussion, highlights the latest ransomware statistics, and provides high-level advice on what to look out for to avoid attacks.
What is Ransomware?
Ransomware is a type of malicious software, or malware, that prevents you from accessing your computer files, systems, or networks and demands you pay a ransom for their return. They can cause costly disruptions to operations and the loss of critical information and data.
Attackers typically do not encrypt all files and leave unencrypted instructions, so victims know how to pay the fee and what the decryption key is. Payments are usually requested via Bitcoin, and fees range anywhere from a few hundred to millions of dollars.
The Infosec Institute has an in-depth look at how several flavors of ransomware encrypt files for those interested in more technical detail.
Ransomware Figures and Statistics
Ransomware statistics show that attacks have been rising for the past decade, but things reached new heights in 2020 due to the pandemic. According to the World Economic Forum, 350 million dollars was impacted in the United States alone, with the average ransom payment over $300,000.
The global damage cost of ransomware has significantly grown from $325 million in 2015 to $20 billion in 2021, and it is predicted to exceed $265 billion by 2031. Today, we are experiencing a ransomware attack every 11 seconds, but this will change to every 2 seconds in 2031.
The increasing use of Internet of Things (IoT) devices across various industries has created a massive new attack surface for ransomware, comprising billions of endpoints. IoT devices often lack tight security controls to stop multiple cyber-attacks. Attackers can easily and quickly adapt their malware to industrial sensors, healthcare devices, or self-driving cars.
BlackFOG has been keeping track of ransomware statistics and damages in 2021. The results show that the United States carries half the share of global attacks, with governments being the primary target, followed by education and healthcare. Interestingly, the number of attacks increased in the first half of 2021 compared to 2020, but it is declining as we are approaching the end of the year.
Ransomware Attack Lifecycle
A ransomware attack happens in several phases:
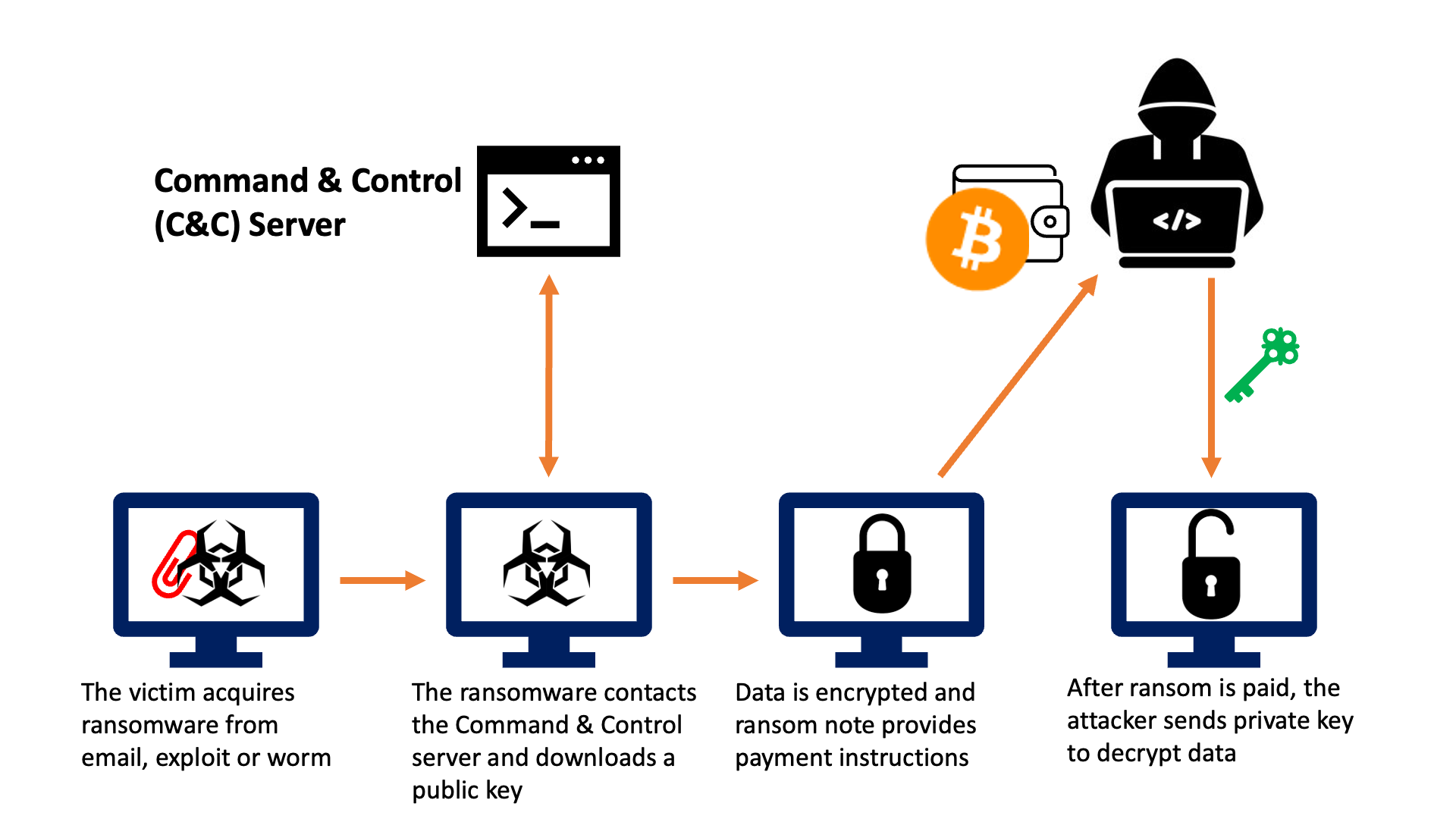
- Initial Foothold: The victim acquires ransomware by opening an infected email attachment, clicking a malicious link, or opening a system exploit.
- Calling Home: The ransomware then connects to the attacker's Command and Control (C&C) server and downloads the encryption key and any other software required – potentially for data exfiltration.
- Data Encryption: Their data is then encrypted, and a ransom payment instruction note is placed and displayed on the victim's machine. Some ransomware steals data and sends it back to the C&C server before encrypting files (more on this to come).
- Decryption Key Delivery: After the victim pays the ransom money, the attacker shares the decryption key, along with decryption software. This step only happens if the attacker holds up their end of the deal.
Types of Ransomware
The two main types of ransomware are:
- Crypto: This kind of ransomware encrypts data and requires a ransom payment in return for a decryption key. Operating system files are often not encrypted so that victims can read the payment instructions.
- Locker: This type of ransomware prevents users from accessing the systems until payment is made. System files are usually the main target here.
The chances of recovering from a Locker-style attack are far greater than Crypto because it's easier to reinstall the operating system and restore access. Attackers may use Locker or Crypto, or in some cases, both at the same time.
What to Look Out For
The best way to avoid being exposed to ransomware or any type of malware is to be a cautious and conscientious computer user. Malware distributors have become increasingly savvy, so really think before:
- Visiting unsafe or suspicious websites
- Opening emails or files from unknown sources
- Clicking on malicious links in email or on social media
Common signs of ransomware infections include:
- Pop-up messages requesting funds or payment to unlock files
- You cannot access your devices, or your login doesn't work for unknown reasons
- Files request a password or a code to open or access them
- Files have moved or are not in their usual folders or locations
- Files have unusual file extensions, or their names or icons have changed to something strange
Ransomware Countermeasures
Some actions you can take to protect yourself or your organization against attacks include:
- Threat-Informed Email Protection: Email is becoming the primary source of many ransomware attacks. Having an email protection system that receives threat intelligence from reputable sources is one of the first mitigation tools. Known ransomware Indicator of Compromises (IoC) is shared between threat-intel authorities and is considered the first defense line.
- Security Awareness and Training: Humans are the weakest link in the cyber defense chain. We get busy and distracted, and we ignore detail and click on links or open attachments. To address this, many organizations use mandatory security awareness training in their Learning Management Systems (LMS) to ensure employees can make the right call when facing threats.
- Knowledge Check: Having awareness and training is proven to be insufficient without regular knowledge checks. A typical approach is running internal phishing campaigns to gauge user readiness and response. In this method, a crafted phishing email is sent to employees. When a user clicks on the link, a warning page is shown to educate the user.
- Remediation Plan: Despite hours of training and constant discussions around ransomware, organizations still become victims of these attacks. The National Institute of Standards and Technology (NIST) provides a reference framework to handle cyber incidents. While implementing detective and protective controls is essential, having a robust "respond" and "recovery" plan is crucial for ransomware attacks. The idea is to have a comprehensive plan and step-by-step runbooks to remediate ransomware attacks and protect against the latest ransomware threats.
- Backup Strategy: When your files are encrypted by ransomware, the timeliest remediation is to recover from backups and resume operation. Having a robust backup strategy and testing your restore plan is key to ensuring things run smoothly should you be hit with an attack.
- Network Segmentation: Breaking a large network into smaller segments helps us contain the ransomware when detected in a part of the network. Many legacy networks are still running as large flat /8 or /16 subnets. As soon as ransomware hits those networks, it can infect many hosts in a short amount of time. It will be hard to segregate and contain the infected endpoints in this situation.
- Isolation and Containment: As mentioned above, the goal is to contain and manage infected hosts as soon as detected. In virtual environments, it may be easier to isolate a host. But in physical environments, you may have to physically disconnect the network connection and work on the computer console to investigate and remediate. The isolation and containment steps for different environments should be clearly defined in the remediation plan and runbooks.
Should We Care About Ransomware?
Yes, looking at ransomware statistics and the news, it is not a question of "if," but "when" a cyber breach will occur. So go ahead and organize that cybersecurity training, review your security tools, refine processes, and put together your remediation plans and runbooks. It's never too late!
Advance Your Career With a Master’s in Cybersecurity
St. Bonaventure's online Master of Science in Cybersecurity program covers essential cybersecurity topics and industry trends.
The curriculum is designed to make you job-ready for the market. Your practical and hands-on learning can be directly used in today's cyber roles and prepare you for what's coming next. Cloud Security, Artificial Intelligence and Machine Learning (AI/ML) are examples of where we are heading.
If you are interested in taking the next step in your career and becoming a cybersecurity expert, schedule an appointment with an Enrollment Advisor today.
Pouya Ghotbi is Associate Director of the Master of Science in Cybersecurity program at St. Bonaventure University. Based in Melbourne, Australia, Pouya is an accomplished security professional with more than 20 years of experience in IT and cybersecurity. In addition to his faculty role, he is a Security, Risk and Compliance Advisor for Amazon Web Services.
